Phishing attacks are becoming increasingly sophisticated, and understanding how to prevent them is crucial for everyone in today’s digital age. These deceptive tactics not only threaten your personal information but can also lead to severe financial consequences. By exploring the various types of phishing attacks and the psychological strategies employed by attackers, we can equip ourselves with the knowledge needed to stay safe online.
In this guide, we will delve into effective prevention strategies, including how to recognize potential phishing emails, implement multi-factor authentication, and secure your personal information. With the right tools and awareness, you can significantly reduce your risk of falling victim to these scams.
Phishing Attack Awareness
Phishing attacks have become a prevalent threat in today’s digital landscape, targeting unsuspecting individuals and organizations alike. Understanding the various types of phishing attacks and the tactics employed by attackers is crucial for enhancing our defenses against such threats. Awareness plays a key role in recognizing these malicious attempts and safeguarding sensitive information.Phishing attacks can take several forms, each designed to deceive victims into divulging personal or financial information.
The most common types include:
Types of Phishing Attacks
Phishing attacks can manifest in different ways, each utilizing distinct methods to trick victims. Here are some prevalent types:
- Email Phishing: This is the most classic form where attackers send fraudulent emails that appear to come from legitimate sources, often mimicking banks or well-known companies.
- Spear Phishing: Unlike generic phishing emails, spear phishing targets specific individuals or organizations, using personal information to make the attack more convincing.
- Whaling: A subtype of spear phishing, whaling specifically targets high-profile individuals such as executives, utilizing highly personalized tactics.
- Vishing: Voice phishing or vishing involves phone calls where attackers impersonate legitimate entities to obtain sensitive information from victims.
- Smishing: This form of phishing uses SMS messages to lure victims into clicking links or providing personal information.
The effectiveness of these attacks often hinges on the psychological tactics used by attackers. By exploiting human emotions and cognitive biases, they can manipulate individuals into acting against their better judgment.
Psychological Tactics Used by Attackers
Phishing attackers employ various psychological tactics to exploit vulnerabilities in human behavior. Understanding these tactics can aid in recognizing and resisting potential attacks. Key tactics include:
- Urgency: Attackers often create a sense of urgency, prompting victims to act quickly without fully considering the implications.
- Fear: Many phishing attempts invoke fear, warning victims of account suspensions or security breaches, compelling them to provide information to “resolve” the issue.
- Trust: By impersonating familiar and trusted organizations, attackers create an illusion of safety that encourages victims to lower their guard.
- Curiosity: Promising enticing rewards or exclusive offers can lure victims into clicking on malicious links, driven by their curiosity.
Real-life phishing attacks highlight the devastating impact these scams can have on individuals and organizations.
Examples of Real-Life Phishing Attacks
Several high-profile phishing attacks have made headlines, showcasing the far-reaching consequences of such threats:
- Target Data Breach (2013): Attackers sent a phishing email to a third-party vendor, gaining access to Target’s network and compromising the personal information of 40 million credit and debit card accounts.
- Google and Facebook Scam (2013-2015): A Lithuanian hacker impersonated a major Taiwanese manufacturer to steal over $100 million from Google and Facebook through fraudulent invoices.
- Ubiquiti Networks (2015): A series of phishing emails caused a loss of $46.7 million when attackers tricked employees into transferring funds to overseas accounts.
These incidents underscore the importance of maintaining a heightened awareness of phishing threats and implementing robust security measures to mitigate the risks associated with them.
Prevention Strategies
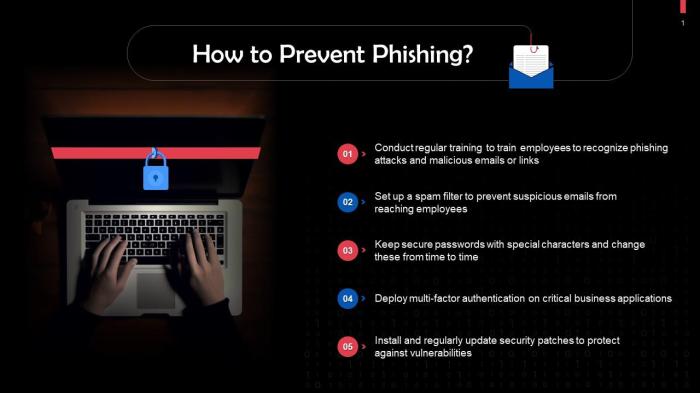
In today’s digital world, recognizing and preventing phishing attacks is crucial for keeping your personal information secure. By understanding the common tactics used by cybercriminals and implementing effective strategies, you can significantly reduce the risk of falling victim to these schemes. Below, we delve into the best practices for identifying phishing emails, securing personal information online, and the importance of multi-factor authentication.
Best Practices for Identifying Phishing Emails
It’s essential to recognize the signs of phishing emails to protect your sensitive information. Cybercriminals often use deceptive tactics that can easily mislead unsuspecting individuals. Here are some key indicators to look out for:
- Check the sender’s email address: Phishing emails often come from addresses that mimic legitimate businesses but may have slight variations or misspellings.
- Look for generic greetings: Legitimate companies usually address you by your name, while phishing emails may use vague greetings like “Dear Customer.”
- Be cautious of urgent language: Many phishing emails create a sense of urgency, prompting immediate action without thinking.
- Inspect links before clicking: Hover over any links to see the actual URL they lead to; if it looks suspicious, don’t click.
- Watch for unexpected attachments: Phishing emails may contain attachments that could introduce malware to your system.
Checklist for Securing Personal Information Online
Implementing a robust security strategy is essential for safeguarding your personal information. Consider the following checklist as a guide to secure your online presence effectively:
- Use strong, unique passwords for each account.
- Enable multi-factor authentication wherever possible.
- Regularly update your software and applications to patch vulnerabilities.
- Be cautious when sharing personal information on social media.
- Monitor your financial accounts regularly for unauthorized transactions.
Importance of Multi-Factor Authentication
Multi-factor authentication (MFA) adds an extra layer of security to your online accounts, making it significantly harder for unauthorized users to gain access. This method requires you to confirm your identity through multiple verification methods, such as a password and a code sent to your mobile device. Implementing MFA can dramatically reduce the likelihood of breaches, even if your password is compromised.To set up multi-factor authentication, follow these steps:
- Access the security settings of your account.
- Select the option for multi-factor authentication.
- Choose your preferred method of verification, such as SMS, email, or an authentication app.
- Follow the prompts to complete the setup, ensuring you have a backup method in case your primary verification method is unavailable.
Enhancing security through multi-factor authentication is a proactive step in protecting your personal information online.
Tools and Resources

Phishing attacks continue to be a prevalent threat in the digital landscape, making it essential to stay informed and equipped with the right tools. Understanding the resources available for ongoing education, as well as software solutions for spam blocking and phishing protection, can significantly enhance your defense against these malicious attempts. Additionally, recognizing the role of social media in phishing attacks and implementing strategies to safeguard your accounts is vital.
Ongoing Education about Phishing Threats
Staying updated on the latest phishing threats is crucial for effective prevention. Various online resources provide valuable information to enhance awareness and education about phishing attacks. These resources include:
- Cybersecurity Blogs: Websites like Krebs on Security and the SANS Internet Storm Center regularly publish articles and insights on new phishing trends and tactics.
- Online Courses: Platforms like Coursera and Udemy offer courses on cybersecurity that cover phishing and other social engineering tactics.
- Webinars and Workshops: Organizations such as the Anti-Phishing Working Group (APWG) host events that educate individuals on current threats and prevention strategies.
Software Solutions for Spam Blocking and Phishing Protection
A variety of software solutions are available to help protect against spam and phishing attacks. These tools enhance email security and can significantly reduce the chances of falling victim to fraudulent schemes. Consider the following options:
- Email Filtering Services: Tools like SpamAssassin and Barracuda provide robust spam filtering to block phishing emails before they reach your inbox.
- Browser Extensions: Extensions such as Web of Trust (WOT) and McAfee WebAdvisor help identify potentially dangerous websites and warn users before they click on harmful links.
- Antivirus Software: Comprehensive antivirus solutions like Norton and Bitdefender include phishing protection features that block malicious websites and notify users of potential threats.
Social Media and Phishing Attacks
Social media platforms are increasingly targeted for phishing attacks, as they often contain personal information that can be exploited by cybercriminals. Understanding how to safeguard your accounts is essential in this digital age. Key strategies include:
- Enable Two-Factor Authentication (2FA): Activating 2FA on social media accounts adds an extra layer of security, making it harder for attackers to gain unauthorized access.
- Be Cautious with Links: Always verify the source of links shared on social media, as these can lead to phishing sites designed to steal personal information.
- Regularly Review Privacy Settings: Adjusting privacy settings on social media can help limit the amount of personal information visible to the public, reducing the risk of phishing.
Closing Notes
In summary, protecting yourself from phishing attacks is not just about being cautious; it’s about being informed and proactive. By applying the tips and strategies discussed, you can enhance your online security and safeguard your sensitive information. Stay alert and educate yourself continuously, as the tactics of attackers evolve, so should your defenses.
Helpful Answers
What are the signs of a phishing email?
Common signs include generic greetings, spelling errors, unusual sender addresses, and urgent requests for personal information.
How can I report a phishing attack?
You can report phishing attempts to your email provider, local authorities, or organizations like the Federal Trade Commission (FTC).
Is it safe to click links in emails from known contacts?
Even from known contacts, be cautious; verify the message before clicking links, as accounts can be compromised.
What is multi-factor authentication?
Multi-factor authentication adds an extra layer of security by requiring two or more verification methods to access an account.
Can antivirus software protect me from phishing attacks?
While antivirus software can help block malicious sites, it should be used alongside other strategies for complete protection.