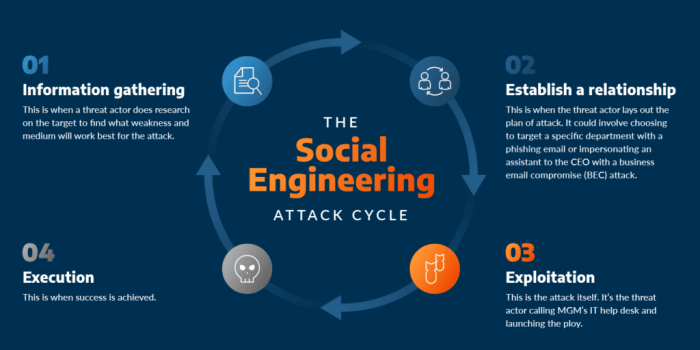
Social engineering attack examples set the stage for this enthralling narrative, inviting readers to dive into the clever tactics used by attackers to manipulate individuals and organizations alike. These attacks exploit human psychology, often revealing how unsuspecting individuals can be led astray without the use of traditional hacking methods.
From phishing schemes that trick users into revealing sensitive information to pretexting scenarios that create elaborate stories, understanding these tactics is crucial in today’s digital landscape. Each example sheds light on the vulnerabilities that can be exploited, emphasizing the need for awareness and proactive measures to safeguard against these deceptive strategies.
Social Engineering Attack Types
Social engineering attacks manipulate human psychology to exploit individuals and organizations. These tactics often bypass technical security measures by tricking people into providing sensitive information. Understanding various attack types is crucial for developing effective countermeasures against such threats.
Phishing Attacks
Phishing is one of the most common forms of social engineering, where attackers impersonate legitimate entities to deceive individuals into revealing personal information. These attacks are typically conducted through emails, messages, or websites that appear authentic.Victims often receive an email that looks like it’s from a trusted source, such as a bank or an online service. This communication usually contains a sense of urgency, prompting the recipient to click on a link or download an attachment.
Once the victim interacts with the fraudulent content, their sensitive data may be compromised. The following elements are frequently found in phishing attacks:
- Imitation of trusted sources: Attackers replicate branding and language used by legitimate organizations.
- Urgency: The message often conveys a sense of immediate action, pressuring the victim to respond quickly.
- Malicious links: Clicking these links can lead to phishing websites designed to harvest credentials.
- Attachments: Malicious files may contain malware that compromises the victim’s system.
According to a report by the Anti-Phishing Working Group, phishing attacks doubled in the past year, underscoring the need for vigilance and education.
Pretexting Scenarios
Pretexting involves creating a fabricated scenario to obtain information from a target. This method often relies on impersonating someone in authority or a trusted figure to build credibility.In pretexting scenarios, the attacker may pose as a company employee, a vendor, or even a government official. The intent is to establish trust and engage the victim in conversation, making it easier to extract sensitive information.
Examples of pretexting include:
- Impersonating tech support: An attacker may call an employee, claiming to be from IT, and ask for login credentials under the pretext of performing maintenance.
- Fake job interviews: A scammer might pose as a recruiter, asking candidates for personal information to complete a supposed background check.
- Charity scams: During crises, attackers may impersonate charitable organizations, urging individuals to provide financial information to donate.
The implications of pretexting can be severe, leading to unauthorized access to sensitive company data or even financial loss.
Real-World Case Studies
Successful social engineering attacks have occurred across various sectors, demonstrating their effectiveness and the importance of awareness.One notable case is the Target data breach in 2013, where attackers used stolen credentials from a third-party vendor to gain access to the retailer’s network. They deployed malware on point-of-sale systems, compromising the credit card information of over 40 million customers. This breach highlighted vulnerabilities in vendor management and the need for robust security protocols.Another example is the 2020 Twitter hack, where attackers used social engineering techniques to gain access to internal tools.
They impersonated Twitter’s IT staff, manipulating employees into resetting accounts of high-profile individuals. This incident underscored the potential for significant reputational damage and financial loss when social engineering tactics are used effectively.These case studies illustrate not only the sophistication of social engineering attacks but also the critical need for ongoing education and security measures within organizations.
Recognizing and Preventing Social Engineering Attacks
Social engineering attacks exploit human psychology to manipulate individuals into divulging sensitive information. Recognizing these attacks is crucial for maintaining personal and organizational security. This section will Artikel common signs of social engineering attempts, effective training strategies, a helpful checklist for threat assessment, and techniques to enhance security against such attacks.Recognizing the signs of social engineering can significantly reduce the chances of falling victim to these tactics.
Social engineers often use various forms of communication—email, phone calls, or even in-person interactions—to execute their schemes. Key indicators of a potential social engineering attempt include:
- Urgency: The attacker may create a false sense of urgency, pressuring individuals to act quickly without thorough consideration.
- Unusual Requests: Requests for sensitive information or actions that deviate from standard procedures often signal a potential threat.
- Unknown Sources: Emails or calls from unfamiliar contacts or unexpected communication from known sources can raise red flags.
- Emotional Manipulation: Attackers might play on emotions, using fear or sympathy to coerce individuals into compliance.
Effectively training employees to identify social engineering tactics is essential for building a resilient organizational culture. Training programs should focus on:
- Real-life Scenarios: Incorporating case studies of past social engineering incidents helps employees understand how these attacks occur.
- Interactive Workshops: Hands-on activities and role-playing can enhance recognition skills and reinforce learning.
- Regular Updates: Keeping training materials current with emerging threats ensures that knowledge remains relevant and actionable.
- Assessment Tools: Implementing quizzes or simulations can help measure employees’ understanding and readiness to respond to potential threats.
A checklist can assist individuals in assessing potential threats during interactions. Being vigilant and aware of the following points can bolster personal security:
- Verify the identity of the requester before sharing any information.
- Look for inconsistencies in communication—such as mismatched email domains or language usage.
- Be cautious with links and attachments; hover over links to see their real destination before clicking.
- Trust your instincts; if something feels off, investigate further before taking action.
Enhancing personal and organizational security against social engineering attacks requires a multifaceted approach. Effective techniques include:
- Implementing Strong Access Controls: Limiting access to sensitive information according to need can prevent unauthorized disclosures.
- Regular Security Audits: Conducting frequent assessments of security protocols helps identify and rectify vulnerabilities.
- Encouraging a Security-conscious Culture: Fostering an environment where employees feel comfortable reporting suspicious activity can lead to timely interventions.
- Utilizing Technology: Deploying security software to detect phishing attempts and malware can provide an additional layer of protection.
By recognizing the signs of social engineering, training employees effectively, utilizing checklists for threat assessment, and implementing robust security measures, individuals and organizations can fortify their defenses against these deceptive attacks.
Related Topics and Their Connection to Security

In today’s interconnected world, the influence of various digital platforms and marketing strategies cannot be underestimated, especially in the context of social engineering attacks. Understanding how these elements interact with security practices is vital for both individuals and organizations. Delving into the role of social media, search engine marketing, web design, and video marketing offers essential insights into the complexities of maintaining security in our digital landscape.
Role of Social Media in Facilitating Social Engineering Attacks
Social media platforms serve as a goldmine for attackers aiming to exploit human psychology. The accessibility of personal information makes it easier for fraudsters to craft convincing narratives. Users often share details about their lives, interests, and networks, which can be leveraged to create tailored phishing attempts or impersonate trusted contacts.
Targeted impersonation becomes increasingly effective when attackers can reference specific information gleaned from social media profiles.
The following points illustrate the connection between social media and social engineering:
- Information Gathering: Attackers can collect data about potential victims, including their location, employment, and relationships.
- Phishing Opportunities: Customized messages based on personal connections can increase the likelihood of a recipient falling for a scam.
- Reputation Damage: A successful attack can lead to identity theft, which may tarnish the victim’s reputation and financial stability.
Overview of Search Engine Marketing Misuse
Search engine marketing (SEM) can be manipulated to facilitate social engineering attacks. Malicious actors may create deceptive advertisements designed to mislead users into clicking through to harmful sites. This tactic not only undermines trust in legitimate advertising but also highlights the risks associated with online searches.
A poorly managed SEM strategy can lead to increased vulnerability for users seeking genuine products or services.
The misuse of SEM can occur in various forms:
- Ad Spoofing: Attackers can create fake ads that mimic legitimate businesses, leading users to phishing sites.
- Hijacking: Competitors may use targeted s to divert traffic to malicious websites.
- Malware Distribution: Ads may direct users to download harmful software disguised as legitimate applications.
Importance of Web Design and Development in Preventing Vulnerabilities
Effective web design and development play a crucial role in establishing security measures that mitigate social engineering threats. A well-designed website not only enhances user experience but also integrates security features that protect against exploitation.
Security should be a fundamental aspect of web development, rather than an afterthought.
Consider these essential security design principles:
- HTTPS Implementation: Secure connections prevent data interception during transmission, safeguarding user information.
- User Authentication: Strong authentication measures, such as two-factor authentication, can reduce unauthorized access.
- Regular Security Updates: Keeping software and plugins up to date minimizes vulnerabilities that attackers could exploit.
Influence of Video Marketing and Streaming in Creating Awareness Around Security
Video marketing and streaming platforms have emerged as powerful tools for raising awareness about security issues. Engaging visual content can effectively communicate the importance of cybersecurity practices to a broad audience.
Videos can simplify complex security concepts, making them more accessible and relatable for viewers.
Here are ways video marketing contributes to security awareness:
- Educational Content: Tutorials and webinars can help explain the significance of recognizing social engineering tactics.
- Real-Life Scenarios: Case studies presented in video format can illustrate the consequences of neglecting security measures.
- Community Engagement: Platforms allow for interaction through comments and discussions, fostering a community focused on security best practices.
Final Conclusion

In conclusion, social engineering attacks pose a significant threat in an increasingly connected world. By recognizing the signs and employing effective prevention strategies, individuals and organizations can fortify their defenses and minimize risks. Ultimately, staying informed and vigilant is essential to outsmarting those who seek to exploit human trust.
Query Resolution
What is social engineering?
Social engineering is the psychological manipulation of people into performing actions or divulging confidential information, often used by attackers to gain unauthorized access to systems or data.
How can I recognize a phishing attempt?
Look for suspicious email addresses, poor grammar, urgent requests for sensitive information, and unexpected attachments or links, which are common signs of phishing.
What can organizations do to prevent social engineering attacks?
Organizations can conduct regular training programs, create awareness campaigns, and establish clear protocols to help employees recognize and respond to potential social engineering threats.
Are social engineering attacks only digital?
No, social engineering attacks can occur in both digital and physical forms, including phone calls, in-person encounters, and social media platforms.
What is pretexting in social engineering?
Pretexting involves creating a fabricated scenario to obtain information from a target, often using a false identity to build trust and manipulate the individual into sharing sensitive details.